Script Termux adalah kumpulan perintah yang ditulis dalam bahasa pemrograman tertentu dan dijalankan dalam aplikasi Termux di perangkat Android.
Script ini memungkinkan pengguna untuk melakukan berbagai macam tugas tergantung pada fungsinya, seperti Otomatisasi Tugas yaitu untuk menjalankan perintah berulang-ulang tanpa harus mengetikkannya secara manual, misalnya backup data, download file, atau mengirim email.
Sebagai eksekusi program yaitu untuk menjalankan program Linux yang tidak tersedia secara native di Android.
Sebagai pengembangan aplikasi yaitu membangun aplikasi sederhana atau prototipe menggunakan tools dan library yang tersedia di Termux.
Sebagai administrasi sistem yaitu mengelola file dan pengaturan sistem Android dengan granularitas yang lebih tinggi dibandingkan pengaturan bawaan.
Juga digunakan untuk belajar pemrograman yaitu Lingkungan Termux ideal untuk belajar bahasa pemrograman seperti Python, Bash, Javascript, dan lainnya.
Namun, penting untuk dicatat bahwa script Termux juga dapat digunakan untuk keperluan yang berpotensi merugikan.
Seperti Spamming yaitu mengirim pesan atau panggilan massal secara otomatis. Hacking yaitu melakukan upaya akses ilegal ke jaringan atau sistem komputer.
Penipuan yaitu menyamar sebagai pihak resmi atau terpercaya untuk mengelabui korban.
Penggunaan script Termux tergantung pada niat dan tujuan pengguna. Saya menekankan bahwa menggunakan script untuk aktivitas ilegal atau merugikan orang lain sama sekali tidak dianjurkan dan dapat berakibat pada konsekuensi hukum.
Jika Anda tertarik menggunakan script Termux, pastikan untuk memanfaatkannya untuk hal-hal yang positif dan konstruktif.
Ada banyak script yang berfokus pada otomatisasi, pengembangan aplikasi, dan pembelajaran pemrograman.
Komunitas Termux juga sangat aktif dan dapat menjadi sumber bagi script dan dukungan terkait.
Ingatlah, teknologi adalah alat yang dapat digunakan untuk kebaikan atau keburukan. Pilihlah jalan yang positif dan manfaatkan script Termux secara bertanggung jawab.
Script Termux Bobol Wifi
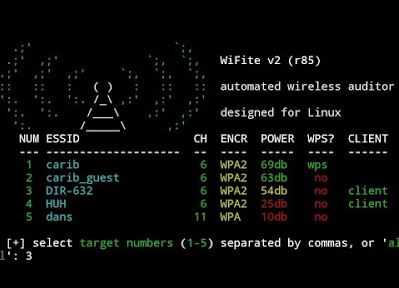
Script Termux bobol wifi adalah sebuah program yang dapat digunakan untuk membobol jaringan wifi yang terlindungi dengan kata sandi.
Dengan menggunakan script ini, kamu dapat mencoba berbagai kombinasi kata sandi secara otomatis hingga menemukan kata sandi yang benar dan berhasil mengakses jaringan wifi tersebut.
Pertama-tama, pastikan bahwa perangkat Android kamu sudah di-root.
Install aplikasi Termux melalui Google Play Store atau sumber lainnya.
Buka aplikasi Termux dan jalankan perintah berikut untuk menginstal paket-paket yang diperlukan: pkg install python pkg install git
Setelah instalasi selesai, jalankan perintah berikut untuk mengunduh script bobol wifi: git clone https://github.com/Cyber-Dioxide/Wifi-Brute.git
Pindah ke direktori script dengan menjalankan perintah berikut: cd Wifi-Brute
Jalankan script dengan perintah berikut: python wifi-brute.py
Script akan mulai mencoba kombinasi kata sandi secara otomatis untuk membobol jaringan wifi yang terkunci. Tunggu hingga script menemukan kata sandi yang benar.
Setelah berhasil, kamu dapat menggunakan kata sandi tersebut untuk mengakses jaringan wifi.
Kelebihan dan Kelemahan Script Termux Bobol Wifi

Sebelum menggunakan script Termux bobol wifi, penting untuk mempertimbangkan kelebihan dan kelemahan dari metode ini.
Berikut adalah beberapa hal yang perlu kamu ketahui:
Kelebihan
Memungkinkan kamu untuk mengakses jaringan wifi yang terkunci dengan mudah dan cepat.
Dapat digunakan sebagai solusi sementara jika kamu lupa kata sandi jaringan wifi sendiri.
Kelemahan
Melanggar privasi orang lain karena membobol jaringan wifi tanpa izin.
Tidak legal dan bisa melanggar undang-undang di beberapa negara.
Membutuhkan waktu yang cukup lama tergantung pada kompleksitas kata sandi.
